Yes, it will show up as Hardship. The Project/Grant will not have an award ID until it is awarded.
Today, ORSP adds commitment lines in the PAF. In Award Management, ORSP will complete an award modification to add new funding information to an award. The new budget line information will appear on the $$$ tab in the Award workspace.
A link to M-Reports is available on the Main tab in Award Management. You can use it to locate more detailed information about the Project/Grant, including any subs under the parent.
PANs and PACs are available on legacy (pre-Award Management) PAFs under Manage Data > View All Award Notices on the PAF workspace.
No. PAF comments will not be migrated over to the Award.
Post-award hardship requests will be submitted through a new award change request type available both on the PAC-R form and the online Award Change Request.
When Award Management goes live in August, fully automated routing of unit requests will not be in place but is planned for a future system upgrade.
Until then, the PI/Project Team will have two options to request an award change:
- Complete the current PACR form, obtain ink signatures, and upload the form using the new Request Action/Modification activity available in the Award workspace
Or - Use the new online Request Action/Modification activity
- Fill out the online Request Action/Modification form, print the form, and obtain ink signatures
- Upload the signed form to your change request and click Submit
No. The PAF exists for historical purposes. Once a PAF is funded, it is for reference only.
All modifications are handled on the award. When a modification is made to the award, the PAF will not change. Links to modifications display on the Mod/ACR tab in the Award workspace.
All PAFs tied to a single award will show up on the Related Records tab. From this tab, you can link back to the PAF if needed.
eRPM will be unavailable during the weekend of the system upgrade and data conversion. Tentatively, the temporary system outage will run from 5:30 p.m. on Friday, August 17 through 6:00 a.m. on Monday, August 20.
eRPM system users (unit and central offices) will be notified in advance of the weekend for the upgrade once the dates are confirmed to allow for planning.
 University of Michigan Supports Adoption of Accelerated Clinical Trial Agreement (ACTA). For those industry partners that agree to use the agreement (and the sponsor must agree to use it), it will decrease contract negotiation time. The other steps, such as budget negotiation, proposal approval form (PAF) processing, and IRB review and approval are still required. And U-M is committed to exploring process improvements and working toward the goal of reducing the total time to opening a clinical trial in all of these areas.
University of Michigan Supports Adoption of Accelerated Clinical Trial Agreement (ACTA). For those industry partners that agree to use the agreement (and the sponsor must agree to use it), it will decrease contract negotiation time. The other steps, such as budget negotiation, proposal approval form (PAF) processing, and IRB review and approval are still required. And U-M is committed to exploring process improvements and working toward the goal of reducing the total time to opening a clinical trial in all of these areas.
The ACTA is a straightforward and unambiguous document that clearly sets forth the contractual obligations of both parties, and presents language which — while perhaps not ideal for either party — is acceptable to both. Adoption and use of the ACTA will expedite the contract negotiation process and reduce the time it takes to start up industry-sponsored, multicenter clinical trials.
HOW TO USE THIS AT U-M
U-M supports and encourage the use of the ACTA for industry-sponsored multi-center clinical trials! Here is what you can do to take advantage:
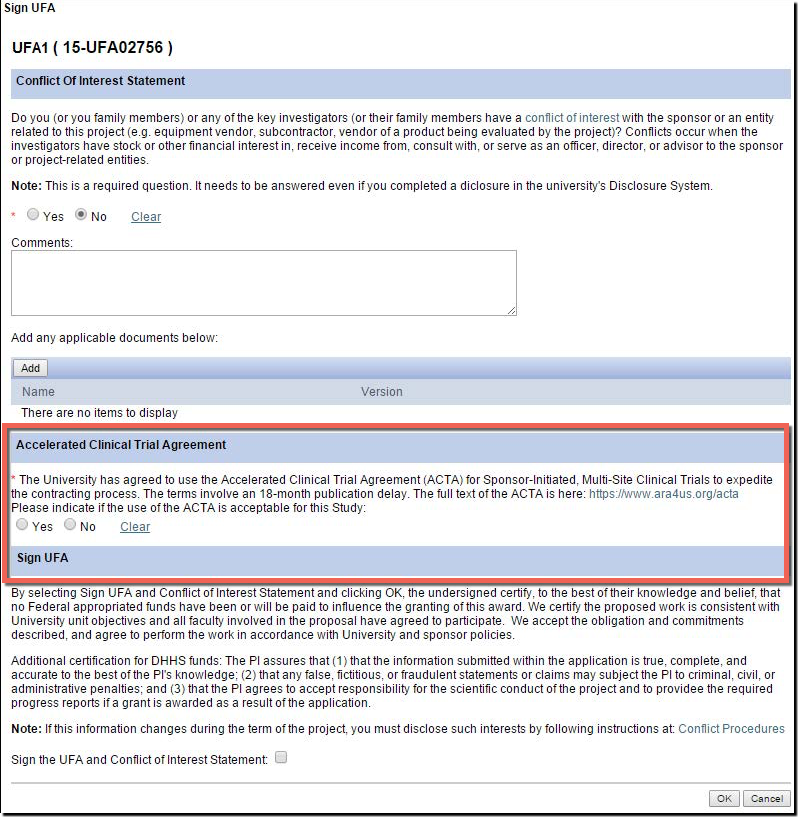
- There is a new question in the eResearch Proposal Management System (eRPM) for the PI added to the "Sign UFA" activity where you may indicate that you would like to attempt the use of the ACTA during the UFA process.
- Answering “Yes” allows ORSP to approach the sponsor to propose the use of the ACTA.
- Additionally, on the Clinical Trials Routing Form (CTRF), the UFA answer will carry over from the NDA. If not answered, ORSP project representatives can help you later pursue the ACTA.
- Award Notices (AWDs) will also carry language to indicate if the ACTA was accepted.
- Contact one of the following ORSP PRs directly when you have questions, if a Sponsor indicates an interest in using the ACTA, or if a Sponsor would like a template agreement to review.
You can review the language in the agreement from the ACTA Website(link is external). The ACTA is not the promise of a full solution to industry-initiated clinical trial contracting, but it can help reduce one part of the process.
Visit https://umclinicalstudies.org(link is external)/ to learn more about Clinical Trial Studies and participation opportunities.
The CTSUs are trans-departmental business units aligned around common thematics of research. The CTSUs are business units that partner with investigators, their teams, and their departments to ensure the timely and efficient activation and execution of clinical trials at the Medical School. The CTSUs provide the administrative support to allow investigators to focus on the science. More information about the CTSUs is available at the Clinical Trials Support Office website.
The first step is to fill out the CTSU Intake Form. The CTSU will then process your CTA and shepherd your trial through the pre-award processes. The CTSU works closely with the ORSP project representatives (Debra Dill, Lark Haunert, Tricia Haynes, and Mike McAllister) who specialize in clinical trials.
A research study in which one or more human subjects are prospectively assigned to one or more interventions (which may include a placebo or other control) to evaluate the effects of those interventions on health-related biomedical or behavioral outcomes.1
(1) U-M has adopted NIH's definition of clinical trials to track and monitor organizational metrics. See full NIH definition with detailed footnotes(link is external).
The Awards tab (for PI & Project Teams) is where you find awards awaiting action (similar to the PAFs tab). Awards on this tab are grouped by:
- Awards Awaiting PI Signature
- Modifications Awaiting PI Signature
- Change Requests with Required Action
- Awards on Hold
You can find a list of active awards on the Active tab.
No. PAF comments will not be migrated over to the Award.
IRB approval is required for the study, but the IRB does not review the registration record in ClinicalTrials.gov. Once registration on ClinicalTrials.gov is complete, add the NCT # to the IRB application.
Required Informed Consent Language for Applicable Clinical Trials:
Applicable clinical trials must use the unaltered consent template language provided below in the informed consent document:
-
"A description of this clinical trial will be available on http://www.clinicaltrials.gov/, as required by U.S. Law. This Web site will not include information that can identify you. At most, the Web site will include a summary of the results. You can search this Web site at any time."
Required Informed Consent Language for NIH and other Sponsor Requirements for Registration and Reporting
NIH funded clinical trials that began on or after 1/18/2017 must refer to ClinicalTrials.gov in their informed consent document (unless they are conducted under a grant submitted prior to that date, with no competing renewals on or after 1/18/2017). Use the below language:
- “This trial will be registered and may report results on www.ClinicalTrials.gov, a publicly available registry of clinical trials.”
U-M Informed Consent templates contain the above language. Refer to IRMED Informed Consent Template and IRB HSBS Informed Consent Template
Yes, it will show up as Hardship. The Project/Grant will not have an award ID until it is awarded.
Post-award hardship requests will be submitted through a new award change request type available both on the PAC-R form and the online Award Change Request.
You can enter the new end date in the Comments/Instructions for ORSP box. Refer to Award Change Request.
When Award Management goes live in August, fully automated routing of unit requests will not be in place but is planned for a future system upgrade.
Until then, the PI/Project Team will have two options to request an award change:
- Complete the current PACR form, obtain ink signatures, and upload the form using the new Request Action/Modification activity available in the Award workspace
Or - Use the new online Request Action/Modification activity
- Fill out the online Request Action/Modification form, print the form, and obtain ink signatures
- Upload the signed form to your change request and click Submit
No. The PAF exists for historical purposes. Once a PAF is funded, it is for reference only.
All modifications are handled on the award. When a modification is made to the award, the PAF will not change. Links to modifications display on the Modifications tab in the Award workspace.
All PAFs tied to a single award will show up on the Related Records tab. From this tab, you can link back to the PAF if needed.
No. If you update personnel (Investigators or Administrative) on the Award, the related PAF is not updated.
Yes. Click on the Name of the item to edit. Refer to Manage Deliverables.
Both units and ORSP have the ability to create Deliverables.
Units are not required to use Deliverables. You are encouraged to check with your unit about any guidelines or requirements in place regarding the use of Deliverables.
- The AWD Docs tab lists associated award, modification, change request, supporting and other documents, and security plans.
- On the Unit Docs tab, you will see documents uploaded by you or others in your unit with access to the award (e.g., PI). Documents stored here are also visible to central offices.
- The Activity Log tab holds documents added through the Post a Comment activity.
Yes, a "snapshot" of the closed PAFs will be available in a single table in the data warehouse for running queries.
What is getting converted?
- PAFs with Active P/Gs
- Single PAF = New Award/Single P/G
- Multiple PAFs with same P/G = New Award/Single P/G
- (Includes PAFs that are expended but related to an active P/G)
- Includes projects that are complete, but not yet Closed)
- A list of historical PANs and PACs will display on the Modifications tab of the Award record.
- An award modification reference will be created for each historical PAN/PAC.
- All modifications of a project will have a Modification ID in order of the PAN or PAC create date.
- The name of the modification will be the PAF ID on which it was created followed by the PAN/PAC ID (e.g., 18-PAF012345-F055555-01).
- The modification type will start with "Legacy" (e.g., Legacy - PAC Financial, Legacy - Administrative, etc.) to indicate that it is a converted record
- These records are intended for reference only and will not contain any content. The original PAN/PACs, including detailed content, can be found on their respective PAFs.
- An award modification reference will be created for each historical PAN/PAC.
What is NOT getting converted?
- Closed Projects. PAFs will remain in the system in a Closed state.
- Documents - No documents will be moved from the PAF to the Award record. Documents will remain on the PAF for historical reference.
For more details, please see Data Conversion on the ITS website.
The following training resources will be available the week of July 23, 2018, on the eRPM Training and Reference Materials web page:
- Narrated training video with system demonstrations
- Step by step job aids and other helpful documentation
In addition, eRPM users have access today to the eRPM “sandbox”, where you can practice using real data. Please note that data entered in the sandbox will not be reviewed, processed, or approved.
We are also planning to hold two interchanges (one on central campus, one on North Campus) just prior to the go live. Details will be shared once the schedule and locations are confirmed.
- We cannot guarantee we will find and announce every limited funding opportunity.
- We sometimes learn of a limited opportunity belatedly. We will do our best to announce it within a reasonable time.
- If you find a funding opportunity of interest and believe it is limited, but do not see it here or in our archived emails, you still must follow our process. Let us know the opportunity you have found. This process is critical: extra submissions can result in the sponsor's rejection of all from the University of Michigan.
- If the sponsor deadline has not expired, you may be able to still apply. Contact [email protected].
- We will try to work with all interested parties to achieve a satisfactory outcome.
Conflicts of Interest (COI) represent financial or other situations where an individual has an outside interest (e.g., equity in a company, intellectual property, consultant activity with a company) that could affect the design, conduct or reporting of their research. Also refered to as personal or individual COI.
Institutional conflicts of interest (ICOI) represent financial or other situations where the University, as an institution, has an outside interest (e.g., equity in a company doing business with the University) that could affect the design, conduct, reporting, review or oversight of research conducted by its employees or students.
Organizational conflicts of interest (OCI) represent situations where an individual's service or work on behalf of a U.S. government agency or other funding sponsor may provide the University, as an institution, an unfair competitive advantage when other University members apply for a funding opportunity with that agency or sponsor.
A Covered Official of the University is an executive officer, dean, or institute/center director with day-to-day responsibility for the supervision of faculty and staff participating in research conducted at or under the auspices of the University.
The initial award notification will come in an email, and all information that we currently know as PAN (Project Award Notice) or PAC (Project Award Change) will reside in the AWD system. If you wish to have a hard copy printed, your best course of action would be to save the email notification as a PDF.
User Acceptance Testing (UAT). During the UAT process, representatives from the schools/colleges/institutes and central offices (who were involved in the working groups) will be asked to preview the online workflow. Additionally, this is a time to redefine or identify any remaining "offline" business processes. No new functionality is expected to be added during UAT. The UAT process simply ensures that requirements have been met.
The eRA Commons (electronic research administration commons) website, by the National Institutes of Health (NIH), that provides principal investigators and their research staff with online features and tools including the abilities to:
- View a full application
- Review current status of an application
- Check for errors
- View application assignment information
- Obtain PDF copies of applications
- Access copies of previous Notices of Grant Award
Get current information on the program official and the grants management specialist
More information from ORSP about using Grants.gov through the U-M eResearch Proposal System
- Extended definition for federal exemption #2 [pre-2018 Common Rule] (proposed by IRB-HSBS, 2013; adopted by all U-M IRBs)
Federal exemption category 2 applies to projects involving educational tests, surveys, interviews, or observation of public behavior. It does not allow for any other research intervention in conjunction with the durvey, etc., regardless of the risk. U-M exemption #2a expands the federal definition to minimal-risk research with adults that involves a non-invasive intervention followed by data collection vai survey, interview (including focus groups) or observation. Examples of non-invasive interventions include, but are not limited to:- Reading a story or vignette
- Playing an electronic game
- Using a computer program or website
- Watching a video
- Using a robot arm or device
- Being exposed to stimuli, such as color, light or sound (within safe limits)
- Two-year approval periods (proposed by IRB-HSBS, 2007; adopted by IRB-Flint, 2014, IRBMED, 2015)
Federal regulations require continuing review of research at least annually, depending on the degree of risk to the subjects. For research projects posing no more than minimal risk to subjects, U-M postulated that lengthening the review period beyone one year was unlikely to increase risks to subjects. - Exemption for analysis of identifiable data: U-M Exemption #7 [pre-2018 Common Rule] (proposed by IRB-HSBS, 2007; adopted by all U-M IRBs) Federal regulations require annual continuing review for all studies, including minimal risk studies where research activity is limited to analysis of identifiable data. U-M proposed that for research involving no direct interaction or intervention with human subjects, the requirement to submit annual continuing reviews doesn not enhance subject safety. A new exemption category was created to provide appropriate review and subsequent exemption from regulatory oversight. Anticipated benefits included:
- Reduction of administrative workload for investigators
- Reduction of application volume for IRB staff and reviewers
- Reduced turn-around time for application review of U-M Exemption #7 studies
- Pilot of the 2018 Common Rule for non-federally funded research (June 2018-January 2019)
Pilot to evaluate business process changes, validate burden-reducing efforts, and test changes to the IRB application prior to the implementation of the 2018 Common Rule, including:- Implementing new and updated exemption categories (except 7 and 8);
- Implementing new exemption review paths, specifically the "system-generated" determination workflow for exemptions 1, 2, and 3; and
- Removing the requirements for continuing review of expedited studies (i.e., minimal risk studies).
HRPP's criteria for demonstration projects includes:
- The research must be determined to pose no more then minimal risk to subjects.
- The research must not include:
- Federal sponsorship, including federal training grants
- FDA regulated components
- Sponsor or other contractual restrictions requiring adherence to federal regulations for clinical interventions (including clinical behavioral interventions)
- Prisoners as subjects
- NIH-issued Certificates of Confidentiality
- The project must evaluate the impact of procedural improvements, including the:
- Compatibility with the current electronic IRB application
- Ease of training and informing investigators, study teams, and the IRB staff
- Ability to monitor the projects.
- The project must signify the impact of procedural improvements on the research community, such as:
- Elimination of regulatory excess that is not protective of human subjects
- Enhanced regulatory outcomes for minimal risk research
- No increase in effort required for investigators.
Innovations U-M has implemented to date include:
- Streamlining the IRB application paths (i.e., types of applications) in eResearch for:
- Secondary use of existing data/records/specimens
- Exempt human subjects research
- Activities not regulated as human subjects research
- Requests for review by a non-UM IRB.
- Updating IRB policies regarding staff roles for:
- Exempt reviews - authorization for IRB staff to make exempt determinations
- Scheduled Continuing Review (SCR) - authorization for qualified IRB-HSBS staff to conduct expedited review of non-federally funded research.
- Implementing U-M guidelines regarding:
- IRB jurisdiction for classroom activities
- Project types not required IRB oversight (see the HRPP Operations Manual, Part 4).
- Expanding the interpretation of federal exemption category #5 to cover public benefit and service programs sponsored by the State of Michigan.
32 CFR Part 2002 identifies three control levels that guide the safeguarding or dissemination of CUI:
- CUI Basic - requires or permits the agencies to control or protect the information, but provides no specific information security controls
- CUI Specified - requires or permits the agencies to control or protect the information, and provides specific information security controls
- CUI Specified, but with CUI Basic Controls - requires or permits the agencies to control or protect the information, and provides only some of the controls
When the university accepts a contract that includes CUI, the Research Information Security Liaison determines the level of CUI (basic or specified) control required and works with the research team to ensure that the appropriate controls are implemented for the life of the project.
An single IRB-of-Record (sIRB) may charge for their services on a cooperative or multi-site, non-exempt human research project. Estimated expenses are calculated on a case-by-case basis and, if allowed by project sponsor, listed as a direct cost in the budget for a funding proposal and award.
Common IRB services include, but are not limited to:
- IRB Reviews
- Initial review of the research protocol, investigator/site qualifications, informed consent plan and documentation, and subject recruitment materials
- Continuing/annual protocol review (regulatory requirement) for subsequent years of the project
- "Periodic" review of any incident reports (e.g., Adverse Events or ORIOs), as they are filed
- Amendments/modifications - changes to the study that require IRB review
- Administrative Services - letters, study changes not requiring IRB review, etc.
- Site/Project Closeout - review of the final status report, resolution of outstanding issues
- Other - services as applicable to the project, e.g., foreign language translation, etc.
Factors that impact the budget for sIRB services include the number of performance sites, level of risk to the participants of the research and/or to the institution, duration of the study, and more. See the External sIRB fee schedule -sample for an example.
![]() Always contact your U-M IRB to determine the best option and requirements for the sIRB prior to submitting funding proposals for cooperative non-exempt human subjects research.
Always contact your U-M IRB to determine the best option and requirements for the sIRB prior to submitting funding proposals for cooperative non-exempt human subjects research.
Failure to comply may result in contract challenges to, or loss of, the award and result in future ineligibility to be awarded government contracts.
Failure to accurately report the status of compliance could result in charges of fraud and criminal penalties for the individual researcher. In addition, the university could also experience adverse reputational, legal, or financial consequences.
The controls for CUI are only implemented when we have accepted a contractual obligation to implement specified NIST SP 800-171 controls. Federal agencies may issue contract amendments that would require CUI controls at any time after a contract has been accepted. Consequently, information security controls may change during a project's lifecycle, but these new terms would only be effective from the date we contractually accept them.
All implementations of a CUI controlled environment will result in shared responsibilities between ITS, IA, the school/college/unit, and the research program. Housing CUI research in the Yottabyte Research Cloud or a cloud-based solution will only address about ⅔ of the required controls. The remaining ⅓ of controls will be the responsibility of the school/college/unit and the research program. The majority of these controls are policies and procedures the research group must implement along with training for all personnel working with CUI.
NIST 800-171 allows for nonfederal entities to meet CUI security requirements by “isolating CUI into its own security domain by applying architectural design principles.”
In this vein, there is currently an ITS-led project initiative in collaboration with ARC-TS to develop a CUI compliant enclave. The Yottabyte Research Cloud will greatly facilitate data-intensive research by providing a flexible computing cloud for complex computational analyses of data classified as Restricted or High, such as CUI. ITS is also developing a proof of concept for a CUI compliant commercial cloud enclave. This will provide a rapidly deployable alternative when the Yottabyte research cloud cannot support a project's technical requirements.
An overarching compliance program is being developed as a partnership between U-M Information Assurance (IA), University of Michigan Office of Research (UMOR), Michigan Medicine Compliance, Office of General Counsel (OGC) and the schools and colleges most likely to work with CUI. Components of the program will include the development of policy, process, security templates, training, periodic risk assessments (RECONs), and the certification that appropriate controls are in place.
Our experience to date is that, after consultation with contracting agencies, we often are able to eliminate CUI provisions and requirements from the final contract.
A research project may include CUI when the funding source is a federal contract or a subcontract where the prime sponsor is a federal agency. The university enters into approximately 1700 new federal contracts/subcontracts each year, but only a small subset are expected to involve CUI. The Office of Research and Sponsored Projects (ORSP) reviews and negotiates all incoming sponsored research contracts and subcontracts for the university.
When ORSP identifies contract language (normally a DFAR or FAR clause) requiring CUI compliance, it requests a review from the Information Security liaison in the Office of Research Ethics and Compliance. The liaison reviews the contract and research proposal works with the Principal Investigator (PI) to determine the applicability of the clause, and then works with ORSP to clarify precisely what materials are CUI and/or negotiate the clause out of the contract.
A research project may also include CUI if it using data acquired under a Data Use Agreement (DUA) and the data is information the government creates or possesses, or that an entity creates or possesses for or on behalf of the government, and has been classified by the government as CUI.
For the majority of research projects at U-M, our information systems meet the definition of a “nonfederal” information system. It is important to note that federal agencies are specifically prohibited from requiring Information security controls above those specified in 32 CFR 2002 for nonfederal information systems.
NARA charged the National Institute of Standards and Technology (NIST) with developing the information security controls for CUI Basic. These controls are detailed in NIST Special Publication 800-171r1, “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.” This publication draws heavily from two earlier NIST information security standards, FIPS 200 and NIST 800-53, both of which are already significantly accounted for by U-M information security practices.
When the university accepts a contract that includes CUI, we determine the classification of the CUI (basic or specified) and work with the research team to ensure the appropriate controls are implemented for the life of the project.
The National Archives CUI Registry identifies the information considered to be CUI by category/subcategories. A non-exhaustive list of categories includes:
- Controlled technical information with military or space application
- Critical infrastructure information (e.g., energy infrastructure, water systems, etc.)
- Export controlled information or materials used in research
- Nuclear information related to protecting reactors, materials, or security
- Statistical information (e.g., U.S. Census)
- Transportation information (e.g., railroad safety, etc.)
The CUI Registry is the authoritative online repository for information, policy, requirements and guidance on handling CUI.
It is critical to protect sensitive government information, some with national security or U.S. trade implications, to reduce the risks of unauthorized release or misue. Application of and compliance with the information security controls helps protect this information against threats to cyber security, data breaches, or other unauthorized disclosures.
Sign up for The RAP/RAPid newsletters (be sure to also check the box that you wish to receive RAN Updates). You can also join the RA Forum on Slack.